Igor Ljubuncic
on 22 August 2019
Useful security software from the Snap Store
Overall, most Linux distributions offer sane, reasonable defaults that balance security and functionality quite well. However, most of the security mechanisms are transparent, running in the background, and you still might require some additional, practical software to bolster your security array. Back in July, we talked about handy productivity applications available in the Snap Store, and today we’d like to take a glimpse at the security category, and review several cool, interesting snaps.
KeePassXC
Once upon a time, password management was a simple thing. There were few services around, the Internet was a fairly benign place, and we often used the same combo of username and password for many of them. But as the Internet grew and the threat landscape evolved, the habits changed.
In the modern Web landscape, there are thousands of online services, and many sites also require logins to allow you to use their full functionality. With data breaches a common phenomenon nowadays, tech-savvy users have adopted a healthier practice of avoiding credentials re-use. However, this also creates a massive administrative burden, as people now need to memorize hundreds of usernames and their associated passwords.
The solution to this fairly insurmountable challenge is the use of secure, encrypted digital password wallets, which allow you to keep track of your endless list of sites, services and their relevant credentials.
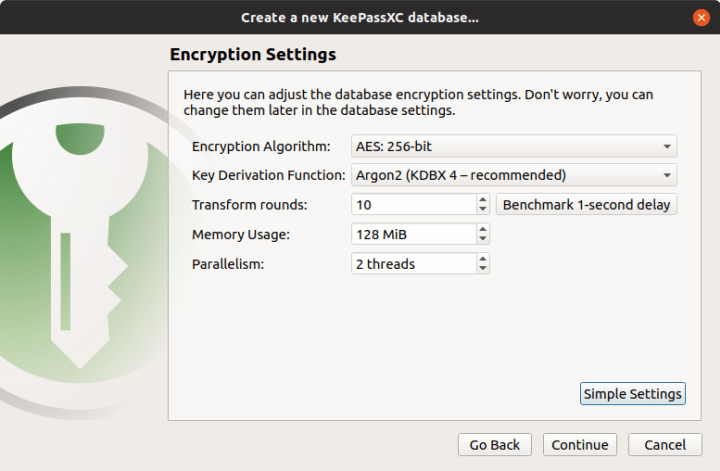
KeePassXC does exactly that. The program comes with a simple, fairly intuitive interface. On first run, you will be able to select your encryption settings, including the ability to use KeePassXC in conjunction with a YubiKey. Once the application is configured, you can then start adding entries, including usernames, passwords, any notes, links to websites, and even attachments. The contents are stored in a database file, which you can easily port or copy, so you also gain an element of extra flexibility – as well as the option to back up your important data.


BitWarden
Side by side with KeepPassXC, BitWarden is a free, open-source password manager. After the application is installed, you need to create an account. Then, you can populate your database (vault) with the entries, including login names, passwords and other details, like card numbers and secure notes. BitWarden uses strong security, and the encrypted vault is synced across devices. This gives you additional portability, as well as an element of necessary redundancy, which is highly important for something like a password database.
BitWarden also includes a Premium version, which offers 1 GB encrypted storage and support for YubiKey and other 2FA hardware devices. The application also allows you to use PIN locking, and arrange your items into folders.

Secrethub-cli
Given that we’ve discussed password management, the next logical step is to talk about collaborative development, configuration files and passwords (secrets) that sometimes need to be used or shared in projects. If you use public repositories (or even private ones), there is always some risk in keeping credentials out in the open.
Secrethub-cli is designed to provide a workaround to this issue by allowing developers to store necessary credentials (like database usernames and passwords) inside encrypted vaults, and then inject them into configuration files only when necessary.

You start by signing up for an account, after which you can use the command-line interface to populate your vault. The next step is to create template files (.tpl) with specifically defined secrets placeholders, and then pass the files to secrethub-cli, which will inject the right credentials based on the provided placeholders (username and password), and then print out the result to the standard output, or if you like, into a service configuration file for your application.
cat example.config.tpl | secrethub inject
This way, the command will run correctly if the right secrethub-cli account is used, but it won’t work for anyone else, allowing reliable sharing of project work. The application is available for free for personal projects.
Wormhole
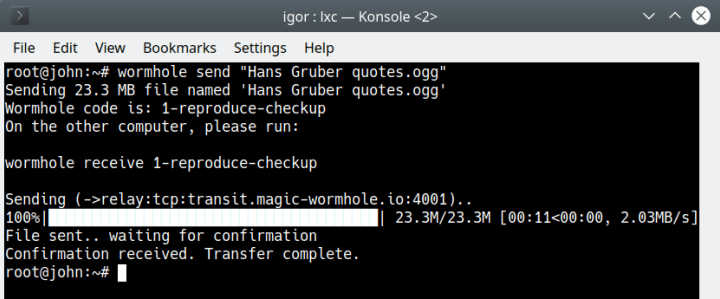
This software might very well be familiar to you, as we’ve discussed Wormhole in greater detail several months ago. It is an application designed to allow two end systems to exchange files in a safe, secure manner. Rather than using email or file sharing services, you can send content to your friends and colleagues directly, using Wormhole codes, which allow the two sides to identify one another and exchange data. Wormhole is a command-line program, but it is relatively simple to use. It also offers unlimited data transfers, and can work with directories too (and not just individual files).

Livepatch
System restarts can be a nuisance, and might lead to a (temporary) loss of productivity. Sometimes though, they are necessary, especially if your machine has just received a slew of security updates. Livepatch is a Canonical tool, offering rebootless kernel patching. It runs as a service on a host and occasionally applies patches to the kernel, which will be used until a full kernel update and the subsequent restart. It is a convenient and practical solution, especially in the mission-critical server environment.
However, home users can benefit from this product too. Livepatch is available for free to Ubuntu users on LTS releases (like 16.04 or 18.04). The only additional requirement is that you do have to register for an Ubuntu SSO account, which will provide you with a token, which you can then use to enable the livepatch service on up to three systems (for free).
snap install canonical-livepatch
canonical-livepatch enable "token"
Once Livepatch is installed and enabled, it will run in the background, doing its job. As a technology, Livepatch fixes cannot be created for every single kernel vulnerability, but a large number of them can be mitigated, dispensing the need for frequent reboots. You can always check the status of the service on the command line, to see that it is working:
canonical-livepatch status

Summary
We hope you enjoyed this piece. Software security often has a somber angle, but we’d like to believe that today’s blog post dispels that notion. The exercise of practicality, data integrity and the ability to protect your important information does not have to be an arduous and difficult task. In fact, you might even enjoy yourself.
We would also suggest you visit the Snap Store and explore; who knows, you might find some rather useful applications that you haven’t really thought of or known before. If you have any comments, please join our forum for a discussion.
Photo by Jason Blackeye on Unsplash.



